Cybersecurity Experts working at some top companies around the world








Academy Reviews :
Duration
Placement Support
Easy EMI
Class Mode
Extra Benefits








Our Diploma in Cyber Security Program is a comprehensive Diploma course that covers from the Beginners to the Advanced level. The training program includes all the major aspects of cybersecurity including ethical hacking, Python programming, web application penetration testing, and network penetration testing. Our Diploma course covers both theoretical and hands-on training on all industry-relevant cybersecurity tools like Nikto, BurpSuite, NMAP etc. The goal of the program is to ensure that our learners are equipped with all the job-ready skills and knowledge required to land a successful career in the domain of cybersecurity.







Our shining stars who have recently attained placement in esteemed companies. DataSpace Academy courses are strategically designed to render a competitive edge in the job market.

 .
.
Need more information about the course details?







Salary range
Companies Hiring



Salary range
Companies hiring



Salary range
Companies hiring



Junior Penetration Tester, Security Engineer












DataSpace Academy courses are available at extremely competitive prices. Our Course Benefits are structured keeping in mind the convenience and budget of students and beginners
Learn to crack job interviews with success and make a positive impression at workplace with our Add-on Packages
4 Days 8 Hours

3 Months

Any query about our program fees?
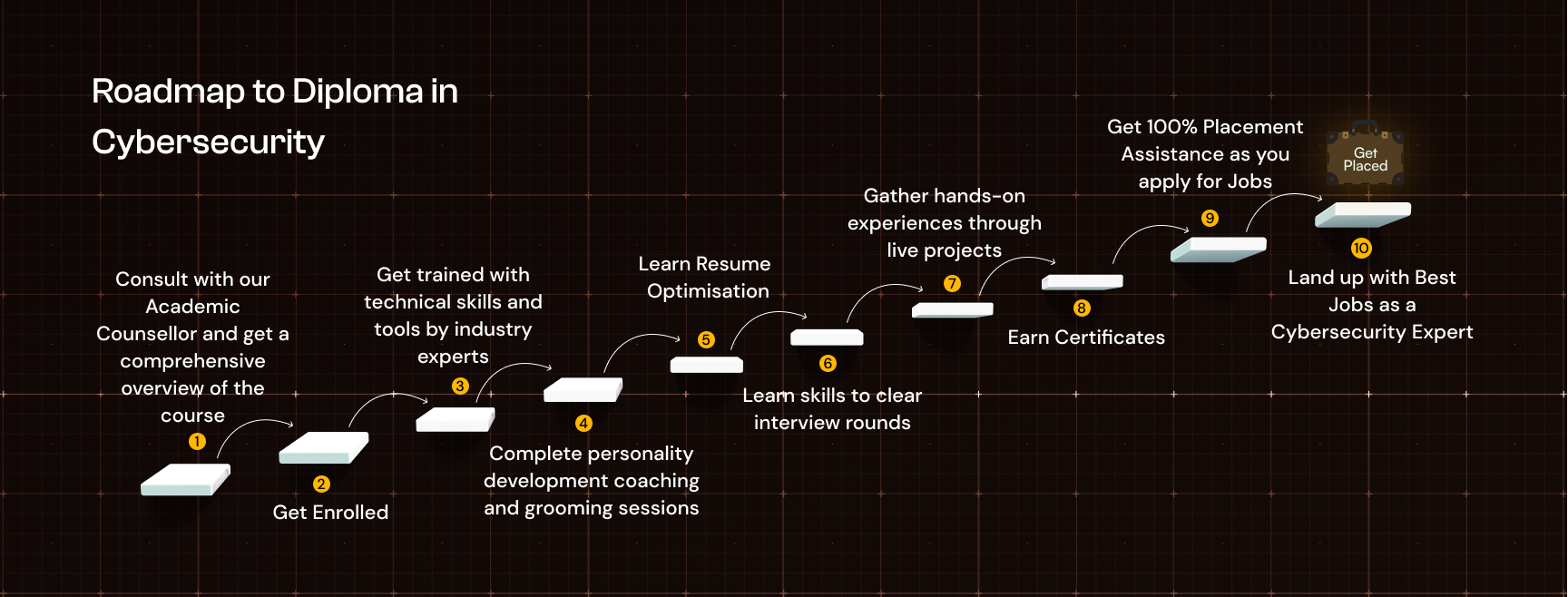
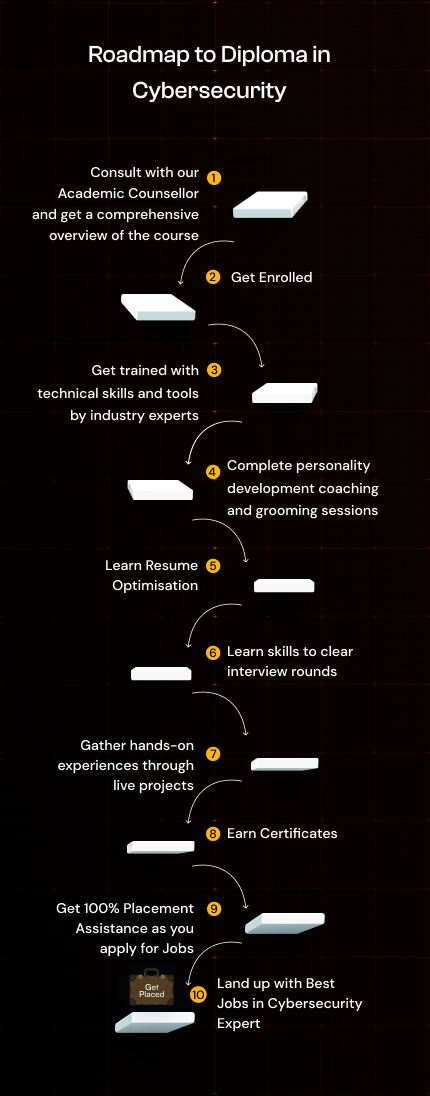
Enroll into your desired course with DataSpace Academy in 4 easy steps

Fill up the
Form

Get a call from our
Academic Counsellor

Get
Consultation

Congratulations for
completing the Enrollment

Senior Cyber Security Analyst
CEH certified, Qualys Guard VM Certification 2019, DevSecOps Trained, DAST & SAST Handling client end to end from taking requirements till providing end report post-false-positive analysis of over 200 applications. Advance Knowledge of professional tools for Network, Source Code Analysis and Web Application Testing. Providing remediations to the clients for the vulnerable issues found during the auditing of the website & Coordinating with the development team for issues closure

Cyber Security Analyst
Raunak K. Bagchi is an experienced Cyber Security Analyst with web application testing and bug-hunting expertise. He has reported several vulnerabilities in platforms such as Bugcrowd, HackerOne, and Integriti and holds certifications in CEHv11 and CCNA essentials. With a strong background in Python programming and manual and automated source code analysis, Raunak is a valuable asset to any cybersecurity project.

Cyber Security Analyst
Soumya Jas is a Web Application Penetration Tester, Bug Bounty Hunter, Blockchain and Python Enthusiast. Additionally, he has an experience in playing CTF games on platforms like Portswigger and HackTheBox. While auditing and securing websites like eBluesoft (https://ebluesoft.com/) he discovered critical vulnerabilities and mitigated those vulnerabilities.

Lead Network Analyst & Cloud Support Engineer, AWS Solution Architect, CCNA(Cisco Certified), MICROSOFT Azure Fundamental
A dynamic AWS Solution Architect, Soumya is also an award-winning AWS and CCNA mentor. He comes with a demonstrated history of working in the information technology and services industry, with specialisation in Mathematics, Computer Networking, Networking, Computer Hardware, Microsoft Office, and Cloud Computing (AWS). He is especially revered for his extraordinary ability to demystify complex CCNA and AWS concepts, making them accessible to learners of all backgrounds and experience levels. A passionate mentor, Soumya is loved by both his students fellow mentors.
We Help you quench your thirst for knowledge by providing you with our specially tailored certifications. Our highly qualified instructors, dedicated staff and 24/7 available helpline are the main reasons why we are the go-to training provider for you.

Industry Experts
Learn from Industry Experts with Years of Expertise in the related field.

Placement Support
Placement Support for successful completion of courses and certification.

Job-Ready Course Curriculum
Specially tailored Certification Course equipped with in-demand industry skills.

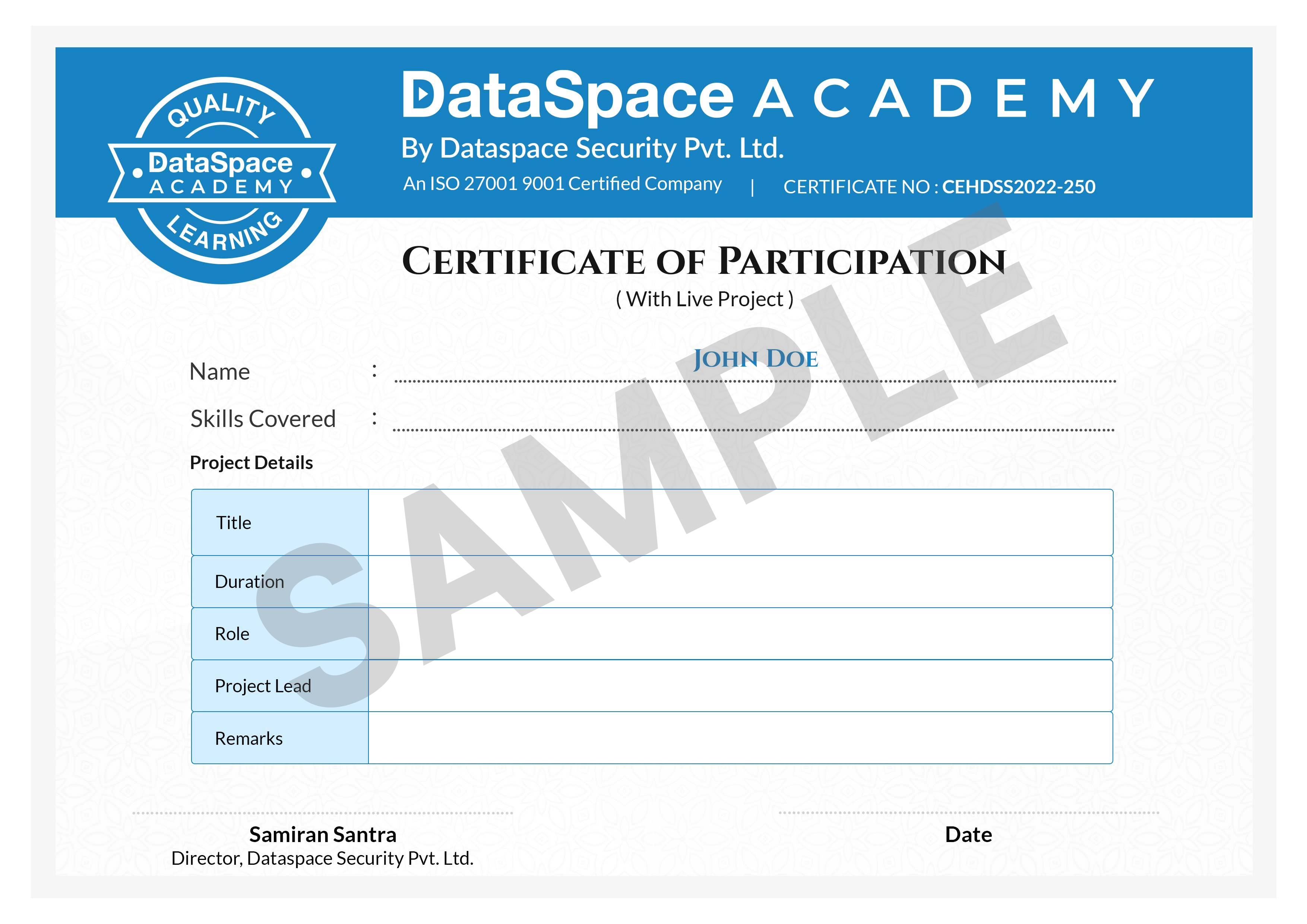
Real Time Projects
Practice on Real Time Projects which can be showcased to future recruiters.

Lab based Classes
100% practical and lab-based classes (available online & offline)

24x7 Support
The course comes with round-the-clock support for doubt-clearing session

Let’s connect with our academic counsellor.
By providing your contact details, you agree to our Terms of Use & Privacy Policy





“I have enrolled for Diploma in cybersecurity. As they told me earlier yes it is an industrial training by industry experts. I took a free class first then I have joined for full course. They are providing flexible slot for everyone that's why I am doing this training or it will be very tuff for me. The sessions are really good & I can recommend to join my friends & everyone.”-





“I am a bca student & did Diploama in Cybersecurity training from DataSpace Academy. The training quality is good no doubt on that. The most important thing which I have seen over here that they are providing good support to everyone as everything is ongoing through online. Almost everything is well & good here”




“Data Space Academy is a very good technical academy. I hav signed for Diploma in Cybersecurity course. All the trainners are very knowledgeable in their domain and they are very friendly in nature. They have sent all the video tutorials after each class. I shall recommend that all the interested person should join the courses provided by the data space security pvt. Ltd. ”




"The Diploma in Cybersecurity Program by DataSpace Academy has been a huge help for my career. This is especially because the course focused on not only the technical aspects but also the practical application of the tools. The instructors too have been extremely helpful and friendly."





"I enrolled in the Diploma in Cybersecurity with minimal prior knowledge, and I am amazed at how much I've learned. The course is structured to accommodate beginners. So, even though I am not from a hardcore tech background, I did not have a problem. The support from the course facilitators and the online community was outstanding. The practical labs and simulations were instrumental in building my confidence to tackle real-world cybersecurity challenges. I would like to recommend for anyone serious about entering the cybersecurity field. "





“The course structure was well-organized, and the pace was just right. The instructors were experts in their field; the practical exercises and simulations were invaluable in helping me apply what I learned. I would highly recommend this course to anyone looking to enter the cybersecurity field or enhance their existing knowledge. ”





"The course content was comprehensive, covering everything from network security to ethical hacking. The instructors were knowledgeable and approachable, always willing to help with any questions. I particularly enjoyed the hands-on labs and real-world case studies, which made the learning practical and engaging."





"It was a huge experience to take the Diploma in Cybersecurity Course from DataSpace Academy. The trainers were extremely helpful. It was good that we got to develop practical skills. I will recommend this course to everybody looking to start in cybersecurity. "




"The Diploma in Cybersecurity course by DataSpace Academy transformed my career. I was having a hard time in finding the right track after my high school and I am glad that I came across DataSpace Academy. The instructors provided in-depth explanations, and the interactive discussions in class enhanced my problem-solving skills. The course not only focused on technical aspects but also emphasized the importance of hands-on skills through live projects. The grooming session provided during the course was an added bonus. "








Have some doubts? Lets Clear!
There is no such hard-and-fast prerequisite to enroll in the course. The course starts with the fundamentals of Cybersecurity so that learners from non-IT background can also join the course.
This course does not require prior technical knowledge. Aspiring learners from any academic background can sign up for the course
For details on seasonal discounts and special offers, please consult with our academic counseling team.
DataSpace Academy provides Internship opportunities and placement assistance based on the merit of the student on successful completion of the course.
After completing the course, our learners will be able to work as Cybersecurity Analyst, Penetration Tester, Cybersecurity Engineer, Cybersecurity Architect, and so on.