[br]The year was 2009. The first block of Bitcoin came into existence and Barack Obama was sworn in as the 44th president of the United States. Amidst these groundbreaking changes, the world woke up to the news of a high-profile scandal - the Stuxnet - a devastating virus attack on the nuclear program of Iran. According to the reports, an employee at the Natanz uranium enrichment plant allegedly ran USB attacks into the control system. Once inserted, the virus-laden (Stuxnet) USB destroyed the uranium centrifuges and derailed the entire nuclear program.
A removable USB driver is usually the default tool for sending and receiving data. But threat actors often use this small, unsuspecting device to run cybersecurity threats. They prefer using removable media devices for establishing remote connectivity, extracting data, or overtaking the system. And often these incidents can lead to serious financial losses. According to an estimate, in 2023, data breaches cost an estimated $4.45 million (Source: 2023 Cost of a Data Breach Report | IBM).
Undoubtedly, USB drives are essential tools but you need to be cautious. The blog here will discuss how to stay safe from bad USB attacks.
This one is simple. It is the transmission of malicious software through USB devices. Also known as the USB drop attack, here the cybercriminals coax the victim to insert an infected USB drive into their computer. Once the USB drive is plugged into the device, the malware is automatically installed. The not-so-harmful malware variants can trigger popup ads in your system or redirect your browser to unfamiliar sites. On the other hand, dangerous kinds can encrypt your system and demand a ransom for unlocking them.
In USB attacks, hackers gain unauthorised entry into computer systems, stealing sensitive information, causing disruptions, or manipulating data for malicious purposes. Researchers have listed 29 types of USB attacks broadly divided into four categories. Here is a listicle of some of the most destructive USB exploitation methods:
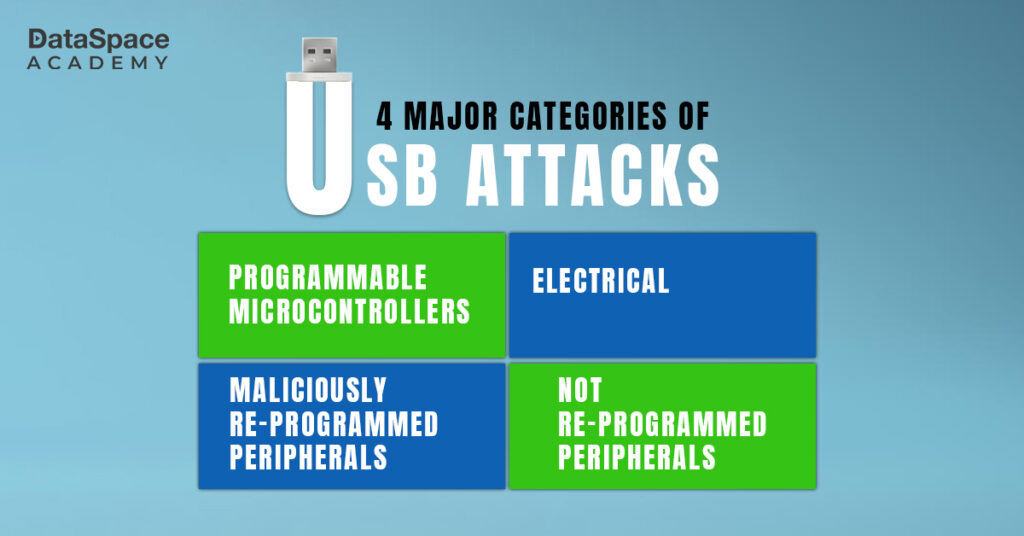
-
-
-
-
Besides the Stuxnet attack, there have been other instances of USB-based attacks either stealing sensitive information or running a malware attack on the system, leading to equipment shutdowns and infections. Here is a list of some of the most notable attacks:
Here is a step-by-step guide on how USB Attacks are conducted:
As we've delved into the intricacies of USB attacks and how they unfold, it's time to focus on strategies to effectively counter these threats. Mitigation involves a combination of robust cybersecurity measures, employee education, and strategic incident response procedures.
Truth be told, malicious USB attacks are fast becoming a harsh reality. What’s worse, these virus or malware-laden devices look the same as your regular USB stick. Thus, businesses have to be slightly more careful while dealing with USB sticks today to fight against USB attacks. However, by installing strict cybersecurity measures, these private organisations and government agencies can secure their defences against these incidents.
Be aware of such incidents and stay protected from online attacks. Start your cyber awareness journey with DataSpace Academy. Join our beginner-friendly
ethical hacking course now!


