Living the digital-first comes with its share of possibilities and limitations. On one hand, it lets you explore a boundless sea of information, stay connected, and search for anything in seconds. On another, there is always the risk of data breach and violation of your digital privacy. In credit: different advanced
types of cyber attacks, all set to turn cyberspace into a roller-coaster ride in the upcoming times.
Let’s open Pandora’s Box of cyber perils waiting for us in this informative blog guide.
Cybercrime shows no signs of slowing down. With malicious actors investing deeply in research and development, 2025 will usher in AI-powered threats that will challenge the safety of our digital existence.
The process of recovering from
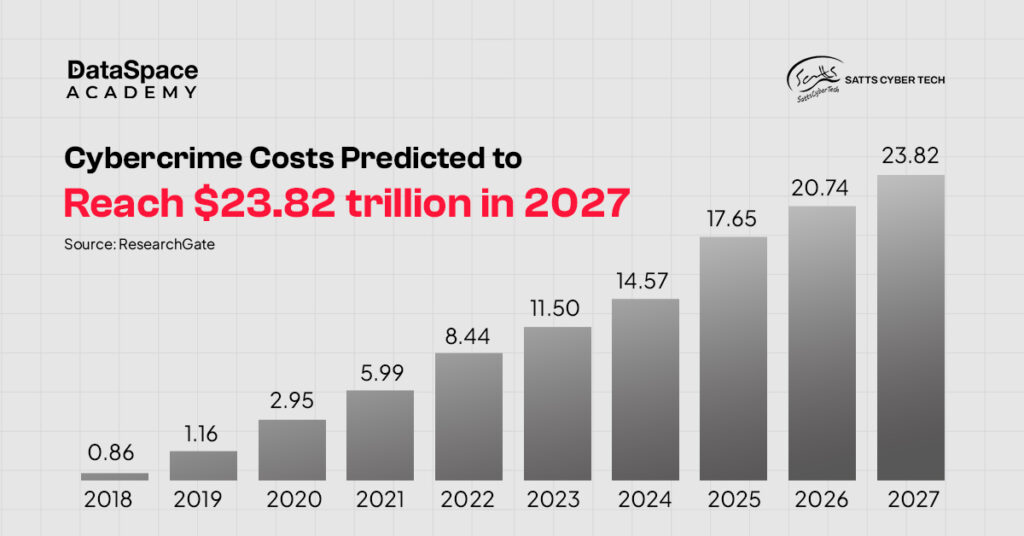
cybercrime is predicted to increase by 15%, eventually totaling $10.5 trillion by 2025 - up from $3 trillion in 2015.
The costs cover a wide range of damages, including data breach and destruction, theft of money and intellectual property. Then, there could be a mighty disruption of business activities. At the same time, legal and investigative expenses continue to mount. Alongside, the magnitude of economic and reputational damage suffered by the victims is undeniable.

Cyber crime instances are now stapled headlines, instilling fear and panic among netizens. And, at the same time, these reports highlight the dire need for robust digital security measures to protect sensitive information and online privacy.
With cyber threats evolving rapidly, individuals and organisations are at constant risk of financial fraud, data breaches, and identity theft. So before we delve into
cyber crime and safety measures, let’s explore the types of cybercrime to be aware of.
Surviving the vulnerable cyber plot is undoubtedly challenging, but no rocket science. All you need is a little awareness and smartness to evade such scams. So here are the expert
safety measures of cyber crime you must follow to stay cyber safe:
Cyberattacks in 2025 will be more sophisticated, especially with the power of AI. The first step of defense starts with proper Cybersecurity education. Empower your cyber safety with industry-leading
cybersecurity certification programs that will equip you with essential skills and knowledge to combat these evolving threats and launch an impactful career in cybersecurity.


 Cyber crime instances are now stapled headlines, instilling fear and panic among netizens. And, at the same time, these reports highlight the dire need for robust digital security measures to protect sensitive information and online privacy.
With cyber threats evolving rapidly, individuals and organisations are at constant risk of financial fraud, data breaches, and identity theft. So before we delve into cyber crime and safety measures, let’s explore the types of cybercrime to be aware of.
Cyber crime instances are now stapled headlines, instilling fear and panic among netizens. And, at the same time, these reports highlight the dire need for robust digital security measures to protect sensitive information and online privacy.
With cyber threats evolving rapidly, individuals and organisations are at constant risk of financial fraud, data breaches, and identity theft. So before we delve into cyber crime and safety measures, let’s explore the types of cybercrime to be aware of.
