Is hacking ethical? In a general view “NO”. However, global businesses are proactively hiring
ethical hackers to keep hackers at bay.
Though it may sound confusing, ethical hackers are currently among the most in-demand professionals - so much so - that according to a recent
US Bureau of Labor Statistics report, growing demand for ethical hackers is predicted to skyrocket by 31% by 2031.
And why not?
2024 has been a roller coaster ride for organisations (small or big), with cyberattacks like data breaches and ransomware creating widespread disruption and fear. This rising level of advanced vulnerabilities has compelled organisations to rely on the skilled army of
certified ethical hacker to empower their defense against malicious minds.
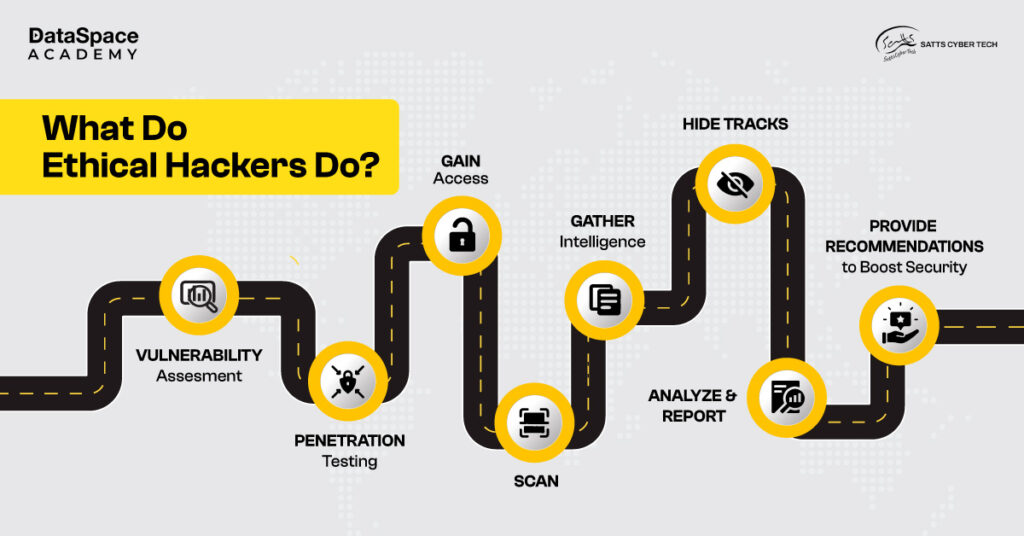
Ethical hackers are also popularly known as white hat hackers. They are skilled cybersecurity professionals who aim to assess security vulnerabilities, find loopholes, and provide recommendations to bolster an organisation's security infrastructure.
Ethical hackers are hired by organisations to hack (with permission) their entire cyber security infrastructure - yet ethically. Unlike hackers, who are aimed to steal data, ethical hackers are driven to an organisation and protect it from illicit hackers.
The sheer difference that makes an ethical hacker an organisation’s dependable resource is its adherence to moral and legal standards. Today, every organisation (small or big) is proactively investing in empowering their cybersecurity infrastructure by hiring skilled, especially certified ethical hackers.

Ethical Hackers are becoming indispensable resources of every modern organisation, especially in data-driven sectors like banks, healthcare, retail, energy & utility, and so on. Today, almost every organisation has a dedicated team of cyber army, where ethical hackers play a pivotal role as the first line of defense against cyber attacks. The primary factor igniting the
demand for ethical hackers is the worldwide occurrence of cybercrimes that have cost companies a staggering $8 trillion. The numbers are expected to rise by nearly $24 trillion by 2027.
Let’s understand how ethical hackers are helping businesses in ensuring a secure cyber infrastructure:
- Fortifying Business Defenses: Ethical hackers proactively identify and patch security vulnerabilities. They act as the digital shield for businesses against increasingly sophisticated cyber threats.
- Outsmart Cyber Criminals: Ethical hackers leverage cutting-edge tools and techniques to outsmart attackers, ensuring businesses are always a step ahead in the cybersecurity game.
- Securing Cloud-Based Operations: As businesses are increasingly migrating to cloud technologies, ethical hackers ensure secure transitions and data protection in the cloud.
- Enhancing AI and IoT Security: Ethical hackers help business in protecting AI systems and IoT devices, which are vital to business operations in 2025.
- Reducing Downtime Costs: By preemptively addressing threats, ethical hackers save businesses from expensive and disruptive downtime caused by cyberattacks.
- Supporting Compliance Efforts: With regulations like GDPR and India’s new data protection laws, ethical hackers help companies maintain compliance with industry standards. Non-compliance to industry standards could leave security gaps and also put the organisation at risk of hefty fines and reputational damage.
- Future-Proofing Business Growth: Ethical hackers equip companies to innovate without fear, fostering growth in an era where cybersecurity is a cornerstone of success.
- Building Customer Trust: Ethical hackers help secure sensitive data and enhance customer confidence, which is critical for brands to stand out in competitive markets.
With businesses growing ever more digital, ethical hackers are the unsung heroes ensuring a safer and more secure future for everyone.
With escalating cyber threats, the demand for certified ethical hackers is growing across various sectors. Adding more to the fear is growing instances of AI-enhanced attacks that are pushing firms to recruit professionals with advanced security expertise. If you are willing to join the race of in-demand AI-powered ethical hackers, this is the time to solidify your skills with
EC Council’s CEHv13. This new-age ethical hacking certification is designed to equip you with the latest threat identification and defense techniques to help you build a rewarding career in AI-driven cyberspace.
Ethical hackers are currently among the most in-demand cybersecurity professionals and the upcoming year is going to unfold a myriad of opportunities for skilled aspirants. Dataspace Academy’s
certified ethical hacker training course is your key to getting started with a high-paying career in 2025.

 Ethical hackers are also popularly known as white hat hackers. They are skilled cybersecurity professionals who aim to assess security vulnerabilities, find loopholes, and provide recommendations to bolster an organisation's security infrastructure.
Ethical hackers are hired by organisations to hack (with permission) their entire cyber security infrastructure - yet ethically. Unlike hackers, who are aimed to steal data, ethical hackers are driven to an organisation and protect it from illicit hackers.
The sheer difference that makes an ethical hacker an organisation’s dependable resource is its adherence to moral and legal standards. Today, every organisation (small or big) is proactively investing in empowering their cybersecurity infrastructure by hiring skilled, especially certified ethical hackers.
Ethical hackers are also popularly known as white hat hackers. They are skilled cybersecurity professionals who aim to assess security vulnerabilities, find loopholes, and provide recommendations to bolster an organisation's security infrastructure.
Ethical hackers are hired by organisations to hack (with permission) their entire cyber security infrastructure - yet ethically. Unlike hackers, who are aimed to steal data, ethical hackers are driven to an organisation and protect it from illicit hackers.
The sheer difference that makes an ethical hacker an organisation’s dependable resource is its adherence to moral and legal standards. Today, every organisation (small or big) is proactively investing in empowering their cybersecurity infrastructure by hiring skilled, especially certified ethical hackers.
 Ethical Hackers are becoming indispensable resources of every modern organisation, especially in data-driven sectors like banks, healthcare, retail, energy & utility, and so on. Today, almost every organisation has a dedicated team of cyber army, where ethical hackers play a pivotal role as the first line of defense against cyber attacks. The primary factor igniting the demand for ethical hackers is the worldwide occurrence of cybercrimes that have cost companies a staggering $8 trillion. The numbers are expected to rise by nearly $24 trillion by 2027.
Let’s understand how ethical hackers are helping businesses in ensuring a secure cyber infrastructure:
Ethical Hackers are becoming indispensable resources of every modern organisation, especially in data-driven sectors like banks, healthcare, retail, energy & utility, and so on. Today, almost every organisation has a dedicated team of cyber army, where ethical hackers play a pivotal role as the first line of defense against cyber attacks. The primary factor igniting the demand for ethical hackers is the worldwide occurrence of cybercrimes that have cost companies a staggering $8 trillion. The numbers are expected to rise by nearly $24 trillion by 2027.
Let’s understand how ethical hackers are helping businesses in ensuring a secure cyber infrastructure:
