By the end of 2023, the global economy will lose close to $8 trillion to cyber attacks (Source: getastra.com). According to the same report, the global loss to cybercrime will grow more than 15% annually, reaching $10.5 trillion by 2025.
With so much at stake, organisations are trying hard to fight against hackers with malicious intent. And they need immediate help. Today organisations are hiring skilled cybersecurity professionals to test and secure their systems and network from hackers. These professionals run penetration testing, often referred to as pen-testing, to find hidden vulnerabilities in the existing network and resolve them. It is a highly important role and this penetration tester career guide can help you land a role in this domain.
Technically, penetration testing is a security assessment method. Here the pen-tester runs an authorised attack to exploit vulnerabilities in a system or network. The ultimate goal of these tests is to identify and assess security weaknesses. Plus, they need to provide remedies for the vulnerabilities as well.
Penetration testing, or pen testing, is a sub-branch of ethical hacking. It helps businesses identify the existing vulnerabilities within their network, servers, devices, or web-based applications. Plus, the pen-tester has to suggest suitable solutions to fix those issues before a hacker discovers them.
Let’s explain pentesting to you in simple terms.
Imagine you have a locker in the bank and you want to keep it safe from thieves. Now a pentester will try to break into the box posing as a robber (say hacker). The agenda is to check the safety and overall security status of the locker. If he finds any problems, he will inform you regarding them so that you can improve the overall security of the bank.
Ideally, the penetration testing process typically involves the following steps:
-
In this phase, the pentester defines the objectives of the tests and identifies the target systems or applications to be tested. The pentester sets clear boundaries and obtains the necessary permissions required for running these scans.
-
The pentester collects intel about the target, including its infrastructure, systems, and potential entry points. This survey helps in understanding the institution’s digital footprint and identifying potential attack points.
-
Testers use various automated and manual techniques to identify vulnerabilities within the target systems. This may involve scanning networks, examining code, or analysing configurations to uncover potential weaknesses.
-
Once vulnerabilities are identified, testers attempt to exploit them to gain unauthorised access or escalate privileges. This phase helps validate the impact of vulnerabilities and demonstrates the potential consequences of a successful attack.
-
Post-Exploitation:
Testers document their findings, including details on all major parameters, such as the vulnerabilities exploited, the data accessed, and the compromised systems. This information is vital for organisations to understand the potential risks and take appropriate remediation measures on time.
-
The final phase involves preparing a detailed report that outlines the findings, recommendations, and steps for improving security. This report serves as a roadmap for organisations to address identified vulnerabilities and enhance their overall security posture.
These penetration testing phases help analysts to determine the overall health status of the network. Penetration testing is a hands-on security assessment approach. By running regular penetration tests, an organisation can proactively identify and fix potential vulnerabilities before hackers.
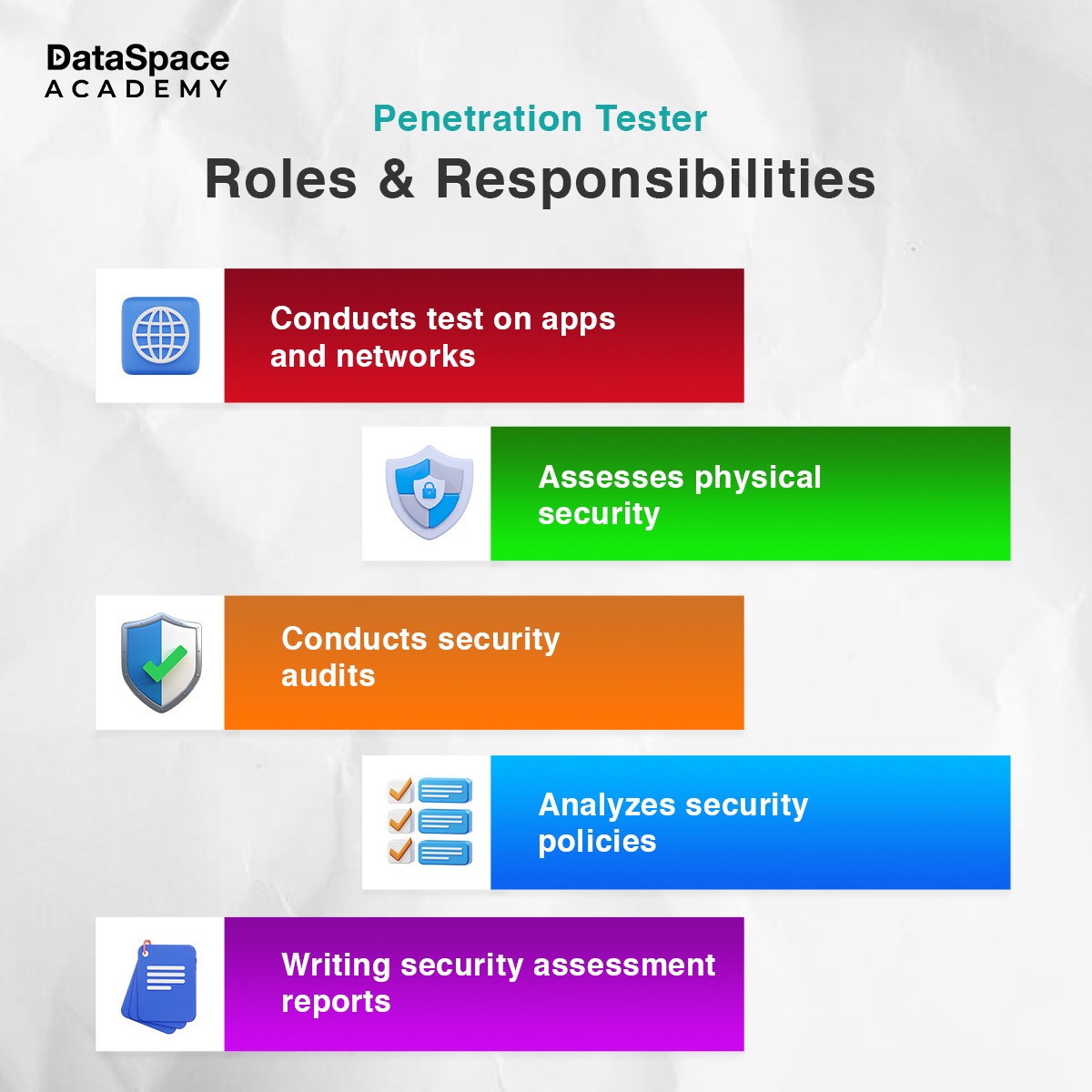
Undoubtedly, penetration testing is a critical step for maintaining the security of the business’s network and other assets. Hence organisations recruit certified penetration tester experts to proactively scan their network and figure out ways to fix security loopholes.
Here are a few reasons why, a career in penetration testing could be a good choice for you:
-
With the increasing importance of cybersecurity across industries, the demand for skilled penetration testers has risen tremendously. Every organisation, from government agencies and financial institutions to tech companies and consulting firms, is hiring talents to identify and mitigate cyber security risks. This high demand translates into excellent job opportunities and increased job security for penetration testers.
-
The security testing services positions command attractive salaries. An entry-level penetration tester can earn close to INR 6 LPA or more, with senior-level roles fetching an even higher remuneration. This makes penetration testing roles financially rewarding.
-
With experience and expertise, penetration testers can progress to more senior positions, such as penetration testing team leads, security consultants, or even cybersecurity managers or CISOs. Additionally, individuals can explore related areas, such as vulnerability management, API pentesting, or threat intelligence to further expand their career prospects.
-
Penetration testing requires a diverse skill set, as well as knowledge of various penetration testing tools like Metasploit or Kali Linux. As a result, professionals in this field are constantly learning and acquiring new skills. The continuous learning process not only keeps the work exciting but also enhances professional growth and opens doors to further specialisation within the cybersecurity domain.
The ever-increasing demand for penetration testing services has exponentially pushed the need for qualified pen testers. Penetration testers can earn a good salary, and they have the opportunity to work in a variety of industries, including finance, healthcare, and government.
Penetration testing jobs are mostly conducted by the cybersecurity team of an organisation. Here is a list of industries that are looking for skilled penetration testers -
- Banks,
- E-commerce,
- Retail,
- Technology,
- Healthcare,
- Government,
- Technology and Software Development.
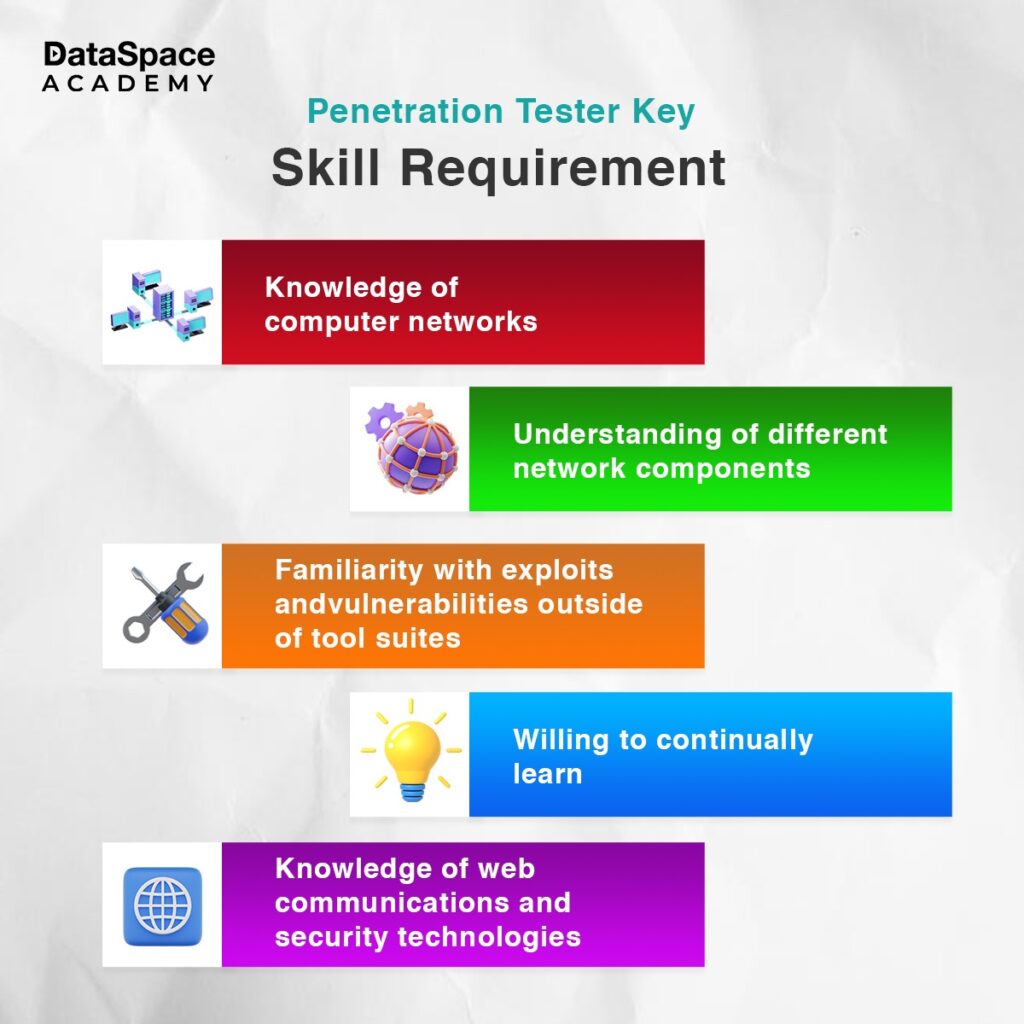
A penetration tester requires a strong understanding of computer networking, operating systems, and web application penetration testing. They must be aware of various tools and techniques that hackers use to exploit the vulnerabilities.
Here is a detailed penetration tester career guide on the different skills required by pentesters:
-
Anyone trying to make it into the penetration testing domain should be familiar with Open Systems Interconnection (OSI) models and computer network architecture. The knowledge of computer networks supports penetration testers to prevent hackers from accessing sensitive information stored within the computer network. Also, understanding network topology maps helps in running diagnostics on the network.
-
A pentester should be aware of the network and hardware components as well as detailed methods for setting up the network for an organisation. They should be able to work with network access controls (NAC) as well.
-
Pentesters should be proficient in programming languages such as Python, Ruby, or JavaScript. These skills enable them to automate tasks, develop custom tools, and analyse code for potential vulnerabilities.
-
Added to expertise in complex web pentesting operations, these professionals should also possess strong communication, analytical, and problem-solving skills. These skills will help them to think creatively and find innovative solutions to security issues. The ability to analyse situations from an attacker's perspective is invaluable in identifying potential attack vectors.
-
With ever-evolving cyber security threats, it is essential for certified pen tester professionals to actively learn new things and gain practical experience to stay ahead of the hackers.
A career in penetration testing follows a well-defined roadmap, starting with foundational knowledge and progressing through various job roles. By continuously upgrading skills, gaining hands-on experience, and earning relevant certifications, professionals can unlock exciting opportunities and earn a competitive salary in this rapidly growing field of cybersecurity.
-
-
-
-
-
-
The basic penetration testing course equips professionals with the necessary tools and knowledge to stay ahead of hackers. These certifications provide a structured approach to identifying vulnerabilities and assessing security measures, enabling organisations to proactively mitigate potential risks. Here are some of the industry-relevant certifications:
-
This EC-Council-accredited certification equips you with the skills to think and act like a hacker. It enables you to look for vulnerabilities within the network, system, or connected devices and implement effective countermeasures.
The CEH certification examination includes 125 questions and takes approximately four hours. A learner can take another six-hour practical test to reinforce learning and fill knowledge gaps.
-
The Penetration Tester Career Guide is incomplete without this course. Here, you are introduced to the fundamentals of penetration testing, covering topics like network penetration testing, cloud penetration testing, and Android penetration testing. Being a mid-level course, anyone applying for the program needs to come with a preliminary understanding of cybersecurity concepts.
Dataspace Academy is a leading organisation for learning penetration testing or ethical hacking. Its recently launched Penetration Testing For Security Engineer certification program is a comprehensive course.
In case you want to learn selective topics on penetration testing, there are dedicated courses on Network Penetration Testing, Web Penetration Application Testing, etc.
-
The Advance Penetration Testing Program is among the best penetration testing certification online or offline courses for candidates who want to scale up their careers. In this course, you get to learn about the lifecycle of an attack from the perspective of a hacker. Developed by industry-experienced pen-testers, the course educates about advanced concepts like API pentesting and red teaming.
-
This course exclusively focuses on penetration testing, making it among the most coveted certifications in the cybersecurity industry. It covers a broad range of security domains, including risk management, access control, and cryptography, making it a valuable addition to your professional profile. But it is also among the toughest penetration testing certifications to crack. The OSCP certification includes an exam that simulates a live network on a private VPN, lasting around 24 hours. It takes 1-2 months of lab practice to crack the exam.
Dataspace Academy has a dedicated OSCP training program that can help you scale this difficult test successfully. In this three-month program, you learn about the most frequently asked concepts necessary to cover the test. Plus, this program provides you with ample practice opportunities for hands-on training.

Penetration Tester Career Guide is incomplete without talking about roadblocks. While pursuing a career in penetration testing in India, students may encounter several roadblocks. Starting with limited educational resources to a lack of specialised courses, the problems could be wide and varied. Here are some of the top challenges faced by students while learning standard penetration testing.
-
In India, the availability of quality pentesting educational resources, books, and courses is highly limited. For most students, access to up-to-date and comprehensive study materials could be a big challenge.
-
Most learners often do not get many opportunities for hands-on experience with various tools.
-
Today, there is a huge shortage of experienced penetration testing trainers who can guide and mentor learners. Finding knowledgeable instructors with practical industry experience in India can be challenging.
However, all these roadblocks can be resolved.
DataSpace Academy, the leading cybersecurity and web penetration testing training institute, is helping aspiring professionals and students overcome these roadblocks. Its multi-level, industry-recognised penetration testing course is designed to help learners become job-ready pentesters for various industries.
The award-winning academy offers both theoretical as well as hands-on training to ensure holistic learning for students. The academy also extends internship opportunities and dedicated placement assistance to help its learners stand out during the job-hunting phase.
 Upto 50% Off on All CoursesValid till 15/07/2025
Upto 50% Off on All CoursesValid till 15/07/2025


