Cybersecurity is no longer just an IT function—it’s a business-critical priority. With organisations facing constant cyber threats, companies are on the hunt for skilled professionals who can safeguard their data, networks, and systems.
If you’re an experienced candidate looking for your next big role, you need to be prepared for
cybersecurity interview questions that go beyond the basics. Employers want to see your expertise in threat mitigation, incident response, compliance, and leadership. This blog will help you navigate
cybersecurity scenario based questions and position yourself as the top choice for senior roles.
Let’s dive into some key insights that will help you ace your next cybersecurity interview!

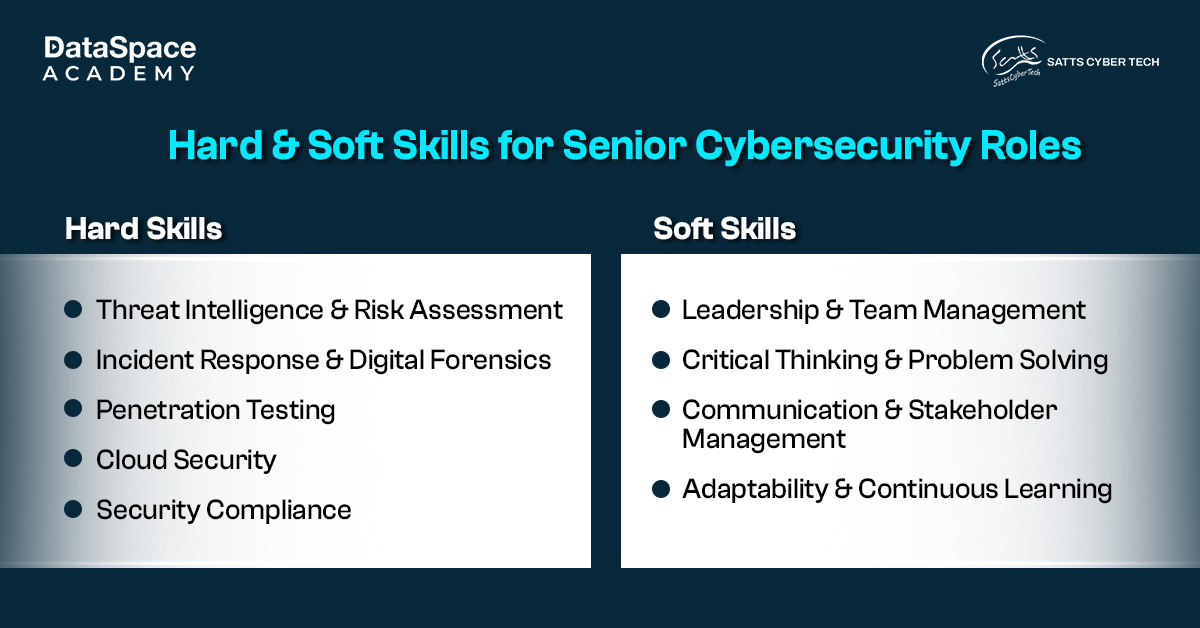
If you're aiming for a senior position in cybersecurity, here are some job roles you can apply for.
Each of these roles demands technical expertise, strategic thinking, and problem-solving skills. Now, let’s explore the
network and security interview questions you may encounter.
1. How do you handle a zero-day attack?
2. Explain the key differences between IDS and IPS
3. What steps would you take after detecting a security breach?
4. Can you describe a real-world cybersecurity incident you managed?
5. How do you ensure compliance with data protection regulations?
6. What are the biggest security risks in cloud computing?
7. How do you stay updated with the latest cybersecurity threats?
Scenario-based questions test how well you apply your knowledge in real-world situations. Here are some examples:
8. If an employee reports a phishing email, what steps would you take?
9. How would you secure a remote workforce?
10. How would you respond to a ransomware attack in an organisation?
 If you're aiming for a senior position in cybersecurity, here are some job roles you can apply for.
If you're aiming for a senior position in cybersecurity, here are some job roles you can apply for.