Cyber attack prevention is currently topping the priority checklist of every organisation (small, big, local, or global). The rising wave of cyber threats, from non-state hackers to even state-sponsored intrusions, has made cyber defense imperative for businesses of all sizes. With critical infrastructures like banks, hospitals, defense firms, and research hubs at risk - it's no wonder companies are investing heavily in safeguarding their billion-dollar digital assets and reputations.
If you are a business owner, keep scrolling to get the latest insights on different types of organisational cyber terror and scalable security approaches.
As technology evolves, so are the mechanisms and impact of cyber risks with the smart integration of AI, bots, and dark web resources. The alarming part is, these sophisticated cyber attacks can easily bypass traditional firewall defenses. As cyber threats continue to diversify to stay as the dominant industrial risks in 2025, here we present some shocking statistics to keep you vigilant.

The repercussions of a well-articulated cyberattack can heavily wreck an organisation’s present and future, followed by irreparable losses. Let’s have a detailed analysis of the colossal damages caused by
different types of cyber attacks.
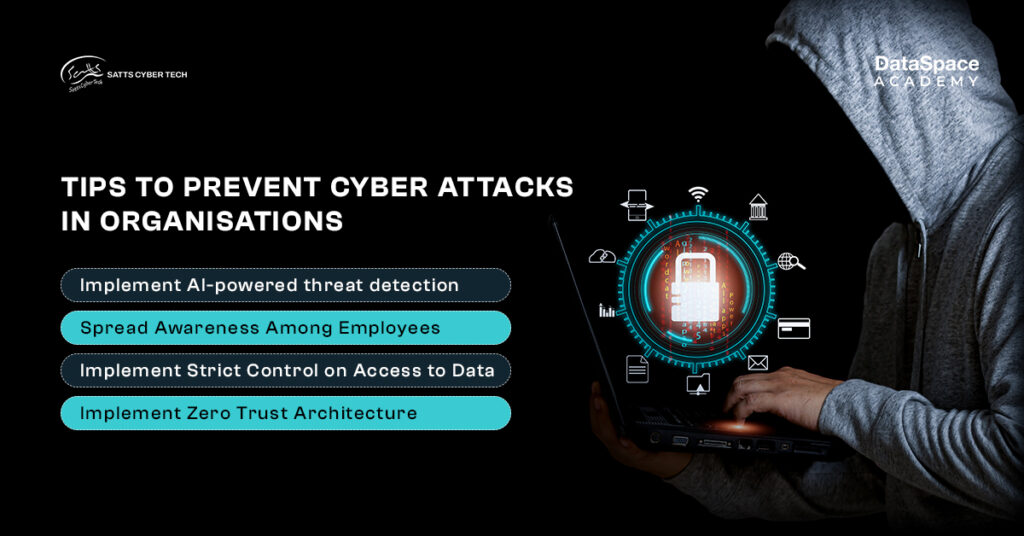
Prevention is always better than cure. So here we present a concrete compilation of practical ways to prevent cyber attacks.
Damage Control with Transparency
Whether a data-driven or service oriented company, it is crucial to have a responsible approach towards customers. Inform them about the company's purpose of collecting customer data and their applications. Assure them about your responsibility in securing their data to create a bond of unbreakable trust.
Cyber attack prevention is a strategic approach by organisations to significantly reduce risks, ensuring organisational resilience against evolving cyberattacks. Investing in a
penetration testing certification course empowers organisations to identify and mitigate vulnerabilities proactively. By training key personnel, businesses can simulate real-world cyber threats, strengthen defenses, and ensure robust security protocols.

 The repercussions of a well-articulated cyberattack can heavily wreck an organisation’s present and future, followed by irreparable losses. Let’s have a detailed analysis of the colossal damages caused by different types of cyber attacks.
The repercussions of a well-articulated cyberattack can heavily wreck an organisation’s present and future, followed by irreparable losses. Let’s have a detailed analysis of the colossal damages caused by different types of cyber attacks.
 Prevention is always better than cure. So here we present a concrete compilation of practical ways to prevent cyber attacks.
Prevention is always better than cure. So here we present a concrete compilation of practical ways to prevent cyber attacks.
