The importance of a firewall in cybersecurity is similar to your home’s security system. As technology advances, so does the nature of threats making your computer- even those with firewall authentication - vulnerable to breaches.
These vulnerabilities have driven significant advancements in firewall technology to protect individual users and enterprises. To counter the growing threat of sophisticated breaches, next-gen firewalls serve as a dependable frontline defense against unauthorised access- safeguarding your devices and enterprise network.
Discover enhanced firewall capabilities for network protection in our detailed blog guide.
Firewalls are designed to monitor incoming and outgoing traffic between trusted internal networks and untrusted external ones, like the Internet. They analyse data packets based on predetermined security protocols and decide whether to allow or block them.
There are different types of firewalls from traditional ones that filter traffic to next-gen firewalls that offer advanced features - like deep packet inspection, intrusion prevention, and even antivirus capabilities. Whether you're an individual worried about protecting personal devices or a business safeguarding critical data, firewalls are an essential part of your security toolkit. They not only prevent unauthorised access but also help manage and control network traffic, effectively securing your digital space.

As mentioned above, there are different types of firewall in network security.
Firewalls are generally categorized into two prime categories: hardware and software.
Hardware firewalls, also known as network firewalls, are physical devices between your system and the internet. They help to inspect inspect both inbound and outbound network traffic.
Software firewalls are built-in security features that come as an added security aide in your computer.
These types of firewall in computer network come in different shapes and sizes based on their filtering method, and functionalities as follows:
- Packet Filtering: A packet filtering firewall is deployed for controlling data flow to and from a network. It allows and blocks the transfer of data based on various parameters- the source address of the packet, its destination address, and the application protocol for transferring data. Packet filtering works by analysing the header of the packet.
- Proxy Service Firewall: This acts as an intermediary between two servers, safeguarding the network by filtering messages at the application layer.
- Stateful Multilayer Inspection (SMLI) Firewall: Stateful inspection of the packet is done based on the preset administrator-defined security norms, state, and port. The process involves a seven-layer model called Open System Interconnection (OSI) and multi-layer inspection of packets at every level. This combined inspection approach makes SMLI highly secured and advanced.
- Next-generation Firewall (NGFW): Gartner Inc. has famously defined next-generation firewall as “deep packet inspection”. It’s a robust blend of application-level inspection, intrusion prevention, external threat intelligence, advanced malware detection, encrypted traffic inspection, and VPN capabilities.
- Unified Threat Management (UTM) Firewall: This firewall is an integration of stateful inspection, intrusion prevention, and antivirus. The tool also carries other additional features like cloud management. It’s simple and user-friendly.
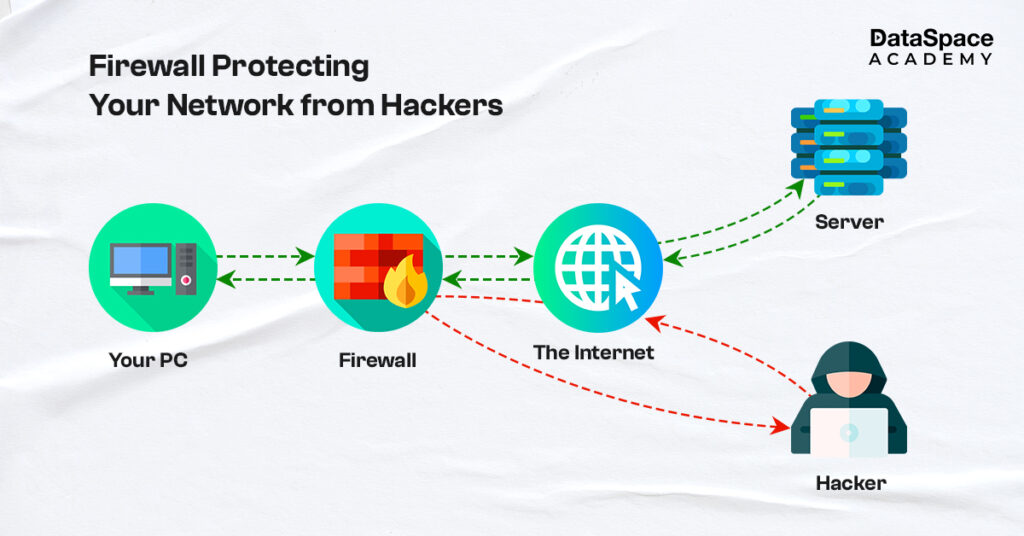
Featuring below the key ways a firewall helps to prevent network attacks:
- Traffic Monitoring
Firewalls constantly monitor incoming and outgoing network traffic by comparing against a set of security rules, allowing or blocking data packets based on predefined security rules.
- Access Control
Firewalls manage and control network access by allowing or denying access to your network based on IP addresses, port numbers, and protocols. This enables only trusted sources to communicate with your network.
- Real-Time Threat Prevention
Modern firewalls come equipped with advanced threat prevention features like Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). These features can detect and block malicious activities in real-time.
- Application Filtering
Firewalls can filter traffic based on specific applications, preventing unauthorised applications from accessing the network. This helps in blocking malware and other harmful software.
- Logging and Alerts
Firewalls keep detailed logs of all traffic and events. They alert network admins about suspicious activities, therefore enabling them to respond quickly.
- VPN Support
Firewalls often support Virtual Private Networks (VPNs), providing secure, encrypted connections for remote users. This ensures data remains safe even when transmitted over unsecured networks.
- User Authentication
Firewalls can enforce user authentication, ensuring that only authorised individuals can access network resources. This adds a layer of security by verifying user identities.
This is how firewalls create a robust defense system, significantly reducing the risk of network attacks and helping maintain the integrity and security of your network.
A firewall is indeed an essential component of network security but can experience glitches due to poor handling. Here is a compilation of mistakes to avoid for a freeze-free security experience:

Firewalls in cybersecurity serve as the first line of defense against malicious attacks and unauthorised access. They ensure data integrity and protect sensitive information from potential threats. For students eager to pursue a career in this dynamic field, enrolling in
cybersecurity certification courses is a smart move. By obtaining certifications, students not only enhance their expertise but also boost their employability, paving the way for a rewarding career in cybersecurity.
 As mentioned above, there are different types of firewall in network security.
As mentioned above, there are different types of firewall in network security.
 Featuring below the key ways a firewall helps to prevent network attacks:
Featuring below the key ways a firewall helps to prevent network attacks:
