Sarah checks into a busy airport. She is early into the airport, and the boarding is yet to start. Sarah is casually strolling through Instagram when her phone beeps “Low Battery”. She plugged into a "free" charging station, not knowing it was a trap for a
juice jacking attack. Unbeknownst to her, hackers extracted the data from her phone, leaving her high and dry before the dark web. Sadly, she learned the hard way: security comes before convenience.
Juice jacking is a form of cyber attack targeting phones and other devices tethered to public charging stations.
Scammers utilise public charging outlets, often found in airports, cafes, and other convenient spots, to break into tethered
smartphones. Many domestic and international agencies, including the FBI, have issued warnings against
cybersecurity dangers associated with using public charging stations.
This blog sheds light on
how does juice jacking work and measures to stay protected from these attacks.
So, what exactly is Juice Jacking? Well, it's a sneaky trick scammers use to extract data from devices when you plug your device into a public charging station.
Scammers have got two main tricks up their sleeves for the
juice jacking attack: tampered hardware and crafty software.
Cybercriminals tamper with the hardware of the charger USB port to install bots or malware into the mobile phone. Once the malware is installed, it can monitor your keystrokes or extract sensitive information to hand over to the hackers.
Now that we know what juice jacking is, let's dive into the nitty-gritty of how these attacks work.
Did You Know?
The term “juice jacking” was first coined in 2011 by investigative journalist Brian Krebs.
A USB port carries five pins:
When a phone is plugged in via USB, the power pin charges the device. However, hackers can manipulate the data transfer pins for
data theft. Once the connection is established between a phone and a computer system, the scammers can access, modify, or copy files from the phone.
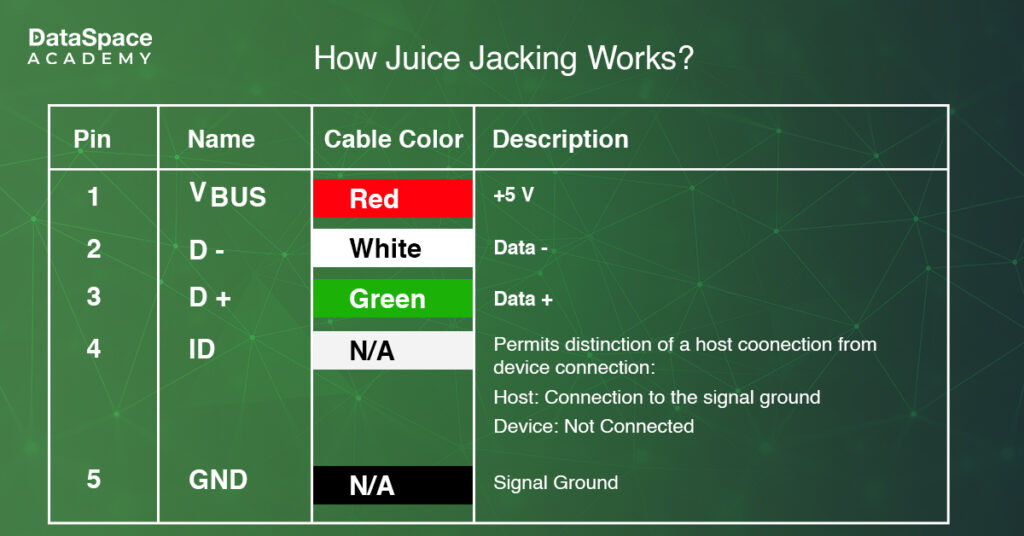
Worse, hackers can inject malware into the phone via these tampered charging stations. Once the malware is installed, it can spy on your activities and cause all sorts of trouble for you.
Join our
cyber security courses online to learn in detail about how these attacks work.
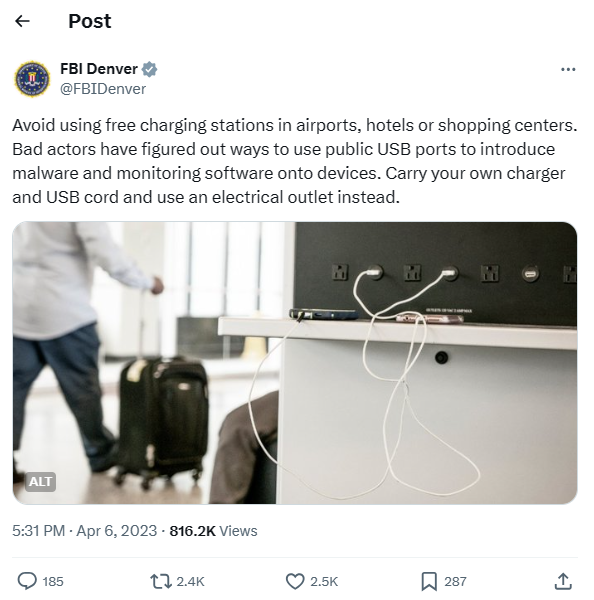
The dangers of Juice Jacking go far beyond the inconvenience of a low battery. Let's explore the potential consequences of falling victim to this cyber threat:

Now that we're aware of the perils of Juice Jacking, let's get down to the business of keeping your precious data safe. Here are some simple yet effective precautions for
preventing juice jacking.
It's not just about charging your device; it's more about safeguarding your digital life.
Sarah learned a lesson the hard way.
But you don’t have to.
Our phone holds the most intimate details of your life. And, scammers taking over your device could be devastating. You need to protect it from scammers at any cost. All you need to do here is to be aware and follow a few simple safety steps while charging your phone in a public campus. By staying informed and cautious, you not only protect yourself but also contribute to keeping your friends and family safe.

 Worse, hackers can inject malware into the phone via these tampered charging stations. Once the malware is installed, it can spy on your activities and cause all sorts of trouble for you.
Worse, hackers can inject malware into the phone via these tampered charging stations. Once the malware is installed, it can spy on your activities and cause all sorts of trouble for you.

 Now that we're aware of the perils of Juice Jacking, let's get down to the business of keeping your precious data safe. Here are some simple yet effective precautions for preventing juice jacking.
Now that we're aware of the perils of Juice Jacking, let's get down to the business of keeping your precious data safe. Here are some simple yet effective precautions for preventing juice jacking.
