Indian organisations suffer
3000+ cyber attacks per week.
Worse, the number is only soaring with every passing year. As of 2025, cyber attacks are way more advanced than what those were 3 years back - and this calls for a robust line of defense. This is where
Zero trust security comes into the picture.
Zero trust is currently the mandatory cyber security mantra, embraced and practiced by major businesses worldwide. Technically speaking, the concept is a strategic cybersecurity model, developed by John Kindervag to secure critical data and systems from any kind of threats (internal and external).
As cloud adoption accelerates with Bring Your Own Device (BYOD) convenience,
zero trust architecture emerges as a cornerstone of modern cybersecurity protocol. Discover why this model is crucial for today's businesses in this comprehensive guide.
“Never trust, always verify”, is the ultimate mantra of
zero trust security model.
The model is more than just preventing breaches. It follows strict guidelines of verifying every user and device that attempts to access an organisation’s resource (data bank or system). The list of access seekers can be on-site employees, remote workers, vendors, partners, and guests. So much so is the level of strict security checks that even insider users have limited access to company resources and applications.
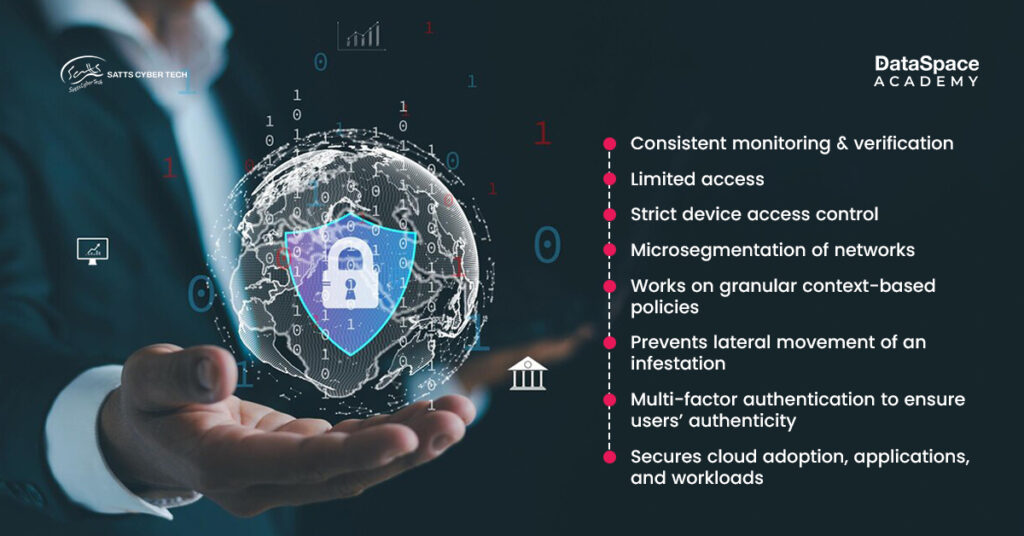
With cyber breaches increasingly jeopardising the global business landscape,
zero trust security has become imperative. Why? Here is a snapshot of its stand-out principles:
Protecting your business from evolving and unexpected cyber threats has become a significant challenge. With the increasing adoption of cloud infrastructure, access to multiple data storages is now available to employees, vendors, and even unverified users. This fast-paced transformation highlights why
zero trust framework is crucial for robust data security.

Here’s a step-by-step look at how it works to protect your business and digital resources.
Zero Trust architecture is the core of cybersecurity practices that not only enhances security but also aligns with the industry's demand for professionals equipped with modern practices.
Pursuing
cybersecurity certifications can significantly bolster your expertise in implementing and managing Zero Trust frameworks. These certifications provide hands-on knowledge, making you a valuable asset in combating advanced threats. By mastering Zero Trust through certified training, you can stay ahead in the ever-evolving landscape of cybersecurity and safeguard critical digital assets effectively.


 Here’s a step-by-step look at how it works to protect your business and digital resources.
Here’s a step-by-step look at how it works to protect your business and digital resources.
