Privacy and data protection have become critical concerns in the ever-dynamic and vulnerable cyberspace. With the increasing amount of information being shared online, securing sensitive data has never been more important. A single event of a data breach can bankrupt an organisation, coupled with added losses such as reputation damage and declining market share. From financial transactions to healthcare records, every piece of information is a potential target for cybercriminals. Data protection involves safeguarding sensitive information from unauthorised access, breaches, or misuse.
With sophisticated breaching techniques on the rise, organisations must adopt robust security measures, including encryption, firewalls, and authentication protocols, to prevent cyber threats. For individuals, understanding the value of their personal data and the risks associated with sharing it online is crucial. As regulations like gdpr in cyber security emphasise the need for enhanced security - it's clear that protecting data is not just a legal requirement, but a fundamental aspect of ensuring safety in the digitally-driven era.
As global enterprises lean more on data for informed decision-making and competitive edge, its growing value is also drawing malicious attention. With time, data breaches have turned into the biggest nightmare for companies, causing significant financial losses and business disruptions.
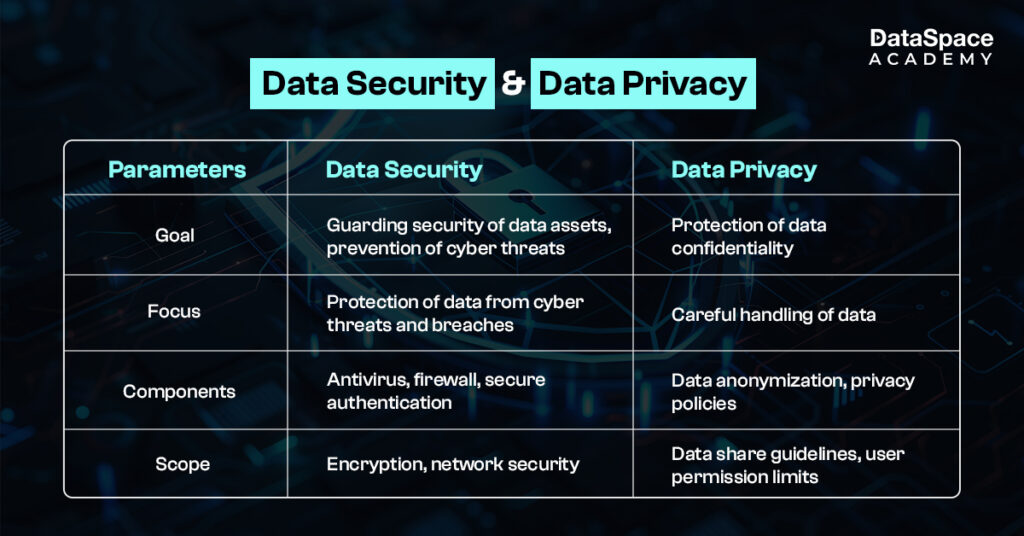
Implementing robust data privacy and security is currently the need of the hour and can help mitigate the following crisis:
 Implementing robust data privacy and security is currently the need of the hour and can help mitigate the following crisis:
Implementing robust data privacy and security is currently the need of the hour and can help mitigate the following crisis:
 This single concern is driving major businesses to adopt and implement data protection factors. Here are seven practical tips for data protection practices against possible breaches:
This single concern is driving major businesses to adopt and implement data protection factors. Here are seven practical tips for data protection practices against possible breaches:
