In the dimly lit parking lot, you discover an abandoned USB drive. Your curiosity piques, and you plug it into your computer. Unknown to you, the USB contains deadly malware. It takes over your system and the laptop screen flashes an ominous message on her screen read: "Your files are now mine”. You are now under
USB attack!
Sounds scary, isn’t it? But this could be a reality. In fact, two recent
USB hijacking incidents -
‘SOGU’ and
‘SNOWYDRIVE’ - have infected millions of computers over the globe.
The blog here aims to shed light on the types and signs of USB attacks, followed by prevention tips.
Cybercriminals use USB Drop Attacks, also known as
USB Attack or
Bad USB Attacks, to spread malicious software through USB devices.
USB attacks involve tricking a person into plugging an infected USB drive into their computer. Once this happens, the harmful software is automatically installed on the computer. Some less harmful types of malware might make annoying pop-up ads appear or take you to strange websites. But the more dangerous ones can lock up your computer and demand money to unlock it.
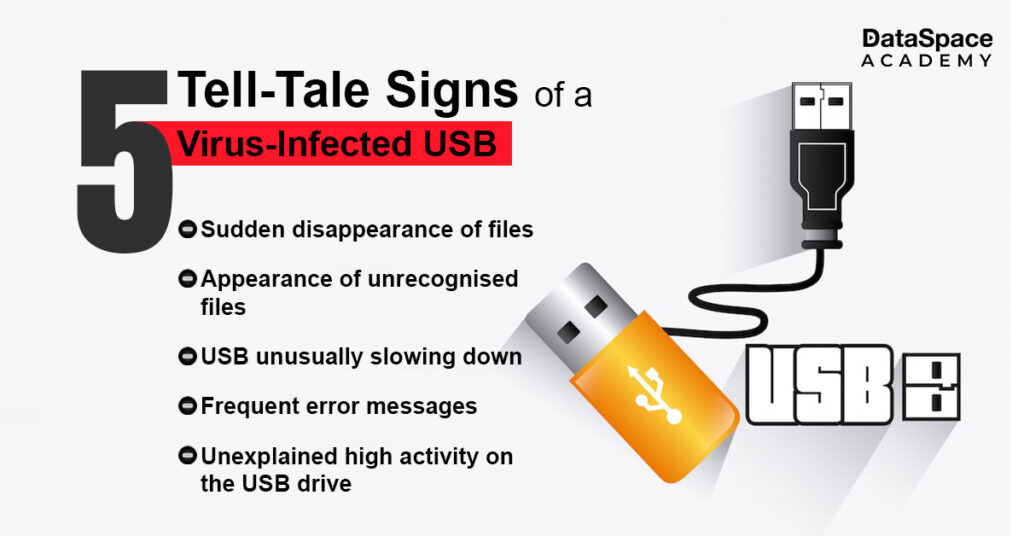
According to researchers at Ben-Gurion University, there are multiple different variants of USB attacks. These
USB attack types are broadly grouped into four categories. Let’s check them out:
Reprogrammable microcontroller USB attacks
Maliciously reprogrammed USB peripheral firmware attacks
Attacks Based on Unprogrammed USB devices
Electrical attacks
Join our
cybersecurity certification course to learn more about these attacks and how to prevent them.
Bad USB attack leads to grave issues, ranging from stealing passwords and accessing sensitive files to damaging a device beyond repair.
Here are some common consequences of a USB attack:

Preventing USB attacks requires strong cybersecurity measures, employee education, and a well-structured incident response plan. Here are some practical tips to defend against these threats:
USB Drives are a small, yet critical tool for data sharing. Unfortunately, hackers are utilising simple, unsuspecting USB devices to spread malware or overtake the system. However, hopefully the guide above will go a long way in keeping your USB and your computer safe.


 Preventing USB attacks requires strong cybersecurity measures, employee education, and a well-structured incident response plan. Here are some practical tips to defend against these threats:
Preventing USB attacks requires strong cybersecurity measures, employee education, and a well-structured incident response plan. Here are some practical tips to defend against these threats:
