Cybersecurity tools are widely used by organisations to shield their security posture. In light of the rising number of
cybersecurity attacks today, every organisation requires security action in place. A systematic security protocol is vital to mitigate
data breaches and to evade the consequences of data loss and breaches. And,
cybersecurity tools are the most crucial weapons of a security defense arsenal. Security analysts take the help of these tools to fix the security gaps of the network infrastructure to avoid unexpected vulnerabilities.
Some of the most popular
cyber security tools are Kali Linux, Nmap, Metasploit, Nessus, Firewall, Aircrack-ng, and more.
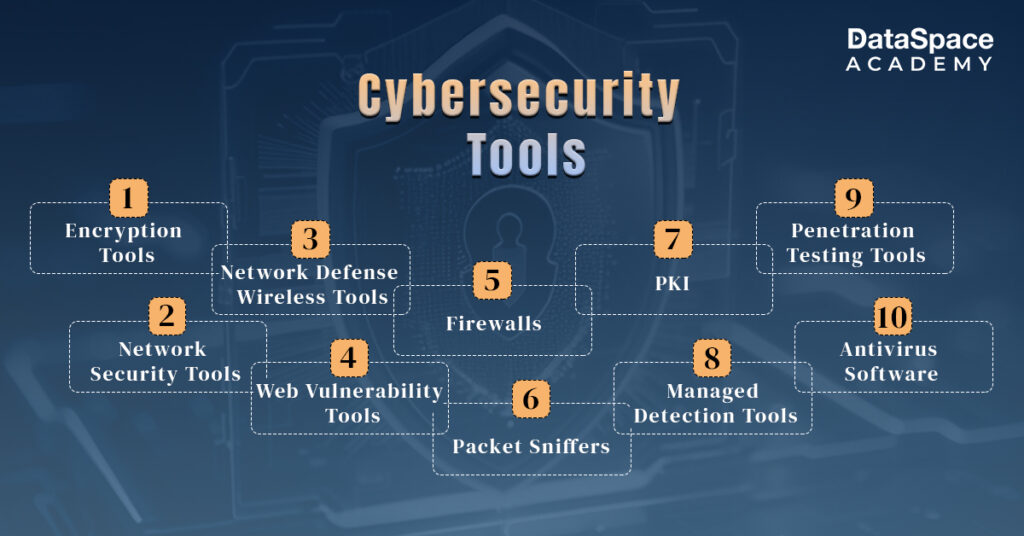
Cybersecurity tools can be majorly divided into 7 categories based on vulnerability assessment and data protection needs. These include -
Cybersecurity experts need to have an excellent understanding of the vulnerability scenario to find the most compatible security tools to thwart
malicious threats. Critical security gaps might command multi-level tools to evade cyberattacks and enforce necessary security measures in place.
But how do you choose the most suitable cybersecurity tool for your network security infrastructure? Well, there are multiple factors to keep in mind for the selection process. The post below sheds light on the most important pointers to keep in mind while choosing cybersecurity tools.
Cyber threats are rapidly evolving as cybercriminals are constantly updating on new technology and deploying sophisticated ways to exploit networks. The choice of cybersecurity tools is dependent on multiple factors.
Cybersecurity professionals generally follow a set of parameters to decide on the appropriate tools to mitigate vulnerabilities.
Here are the major parameters followed by security analysts to choose and implement relevant cybersecurity tools:
Multiple tools are available to secure the network systems. However, one must carry out a thorough risk analysis to gauge the existing security status of the organisation. The process of risk analysis or vulnerability assessment is carried out in three stages.
First, there will be an in-depth audit of available assets which will provide a comprehensive picture of the existing vulnerabilities. In the next step, the cybersecurity analyst will establish the network vulnerabilities. The last step includes the detection of security patches and the launch of a simulated penetration attack to expose vulnerabilities. The final assessment report will help the security analyst find the most suitable tool - as per the specific level of vulnerability.
Your choice of ideal cybersecurity tools will largely depend on your future plan of scaling up the network security infrastructure of your organisation.
So, first, chalk out a plan for the cybersecurity infrastructure. Then, carry out research on the cybersecurity tools in the current market based on their parameters of scalability, reputation, cost, support, and compatibility. Make a comparative analysis of the tools based on the product websites, reviews, case studies, and news reports on new vulnerabilities. The research will help to find the most compatible scalable solutions (cybersecurity tools) that will complement the growing cybersecurity infrastructure of your company.
When it comes to picking security tools, organizations have to be mindful of compliance with legal and regulatory standards. For instance, the healthcare industry complies with the Health Insurance Portability and Accountability Act (HIPAA). This sets standards for protecting the personal identifiable information (PII) of people and also secures the electronic information of the patients.
On the other hand, the retail industry complies with the Payment Card Industry Data Security Standards (PCI DSS). This is chiefly done to protect the data of the cardholder. The PCI DSS regulation also aims to ensure regular testing of networks, maintenance of infosec policy, and implementation of necessary control measures. So, consider the specific regulatory standards of your industry while selecting the most suitable cybersecurity tools for your organisation.
 HIPPA Compliance Rules:
HIPPA Compliance Rules:
Organizations must conduct a thorough study of their security infrastructure to address security breaches and data breach incidents. This will help to analyse the existing solutions that are currently deployed within the organization- especially their strengths and limitations.
Most importantly, the study will help you to locate the old outdated tools to be replaced with new tools to thwart the newly evolved threats.
A tool that is difficult to use may hamper the user experience and also affect the overall security measures implemented by an organisation. Hence the security solutions have to be user-friendly and easily usable to ensure smooth operation.
Carry out a thorough comparison study on multiple tool vendors to find out the most suitable one, as per the required security infrastructure. It is also necessary to locate the risks and trade-offs. The study will further help you to chalk out the ideal plan to devise the cybersecurity protocol of an organisation and monitor its efficacy. Make sure to follow an unbiased approach while making the comparison; the selection of security vendors has to be truly based on their performance and credibility.
There is a wide range of cybersecurity tools in the market but not all would be conducive to your organisation's security infrastructure. You need to be mindful of a list of factors to ensure that you come up with the most suitable tools for optimum security operations.
DataSpace Academy offers job-ready and beginner-friendly
cybersecurity courses that focus on all the major cybersecurity tools in the contemporary market. Learners will be able to attain both theoretical and hands-on training on these tools and build a successful career in cybersecurity.


 HIPPA Compliance Rules:
HIPPA Compliance Rules:
