Standing in today’s time, it won’t be wrong to say that businesses are floating on cloud 9. Businesses of all sizes are switching from on-premise to cloud for enhanced convenience in resource sharing and boosting productivity. Cloud migration is crucial for enabling unlimited access to applications, ensuring prompt & secure data sharing, and promoting seamless collaboration among teams. All these factors make cloud migration the need of the hour.
However, despite the unlimited convenience, the cloud comes with its share of crises. The prime among these is
cloud security concerns that deter businesses from switching to the cloud. But mindfulness about cloud security practices would go a long way in safeguarding cloud resources from prying lenses.
In recent years, cloud computing has witnessed exponential growth, fast becoming the backbone of modern digital infrastructure. With the rapid proliferation of remote work arrangements, there is now an increased reliance on cloud-based services and applications. This increasing pattern in cloud migration has heightened the need for secure access controls and data protection mechanisms. Plus, the rise of hybrid and multi-cloud environments has introduced complexities in managing security across different platforms - necessitating comprehensive strategies for visibility and control.
Additionally, the evolving nature of sophisticated breaches underscores the criticality of implementing proactive security measures such as - encryption, threat detection, and incident response protocols.
Put simply, as organisations continue to leverage cloud technologies to drive innovation and agility, prioritising cloud security is paramount. There is a dire need for powerful security measures to mitigate risks, protect assets, and instil trust among customers and stakeholders.
Cloud security is paramount and requires a combination of threat identification and crisis mitigation strategies. Let’s decode them in brief one by one:
With businesses increasingly banking on cloud, cloud engineers are one of the most sought-after professionals today. To advance your career in cloud computing, enroll in our highly demanding
AWS solution architect course online.

2024 is marked by a surge in highly evolved threats that are challenging the very foundations of cloud security infrastructure. Listing below some of the following:
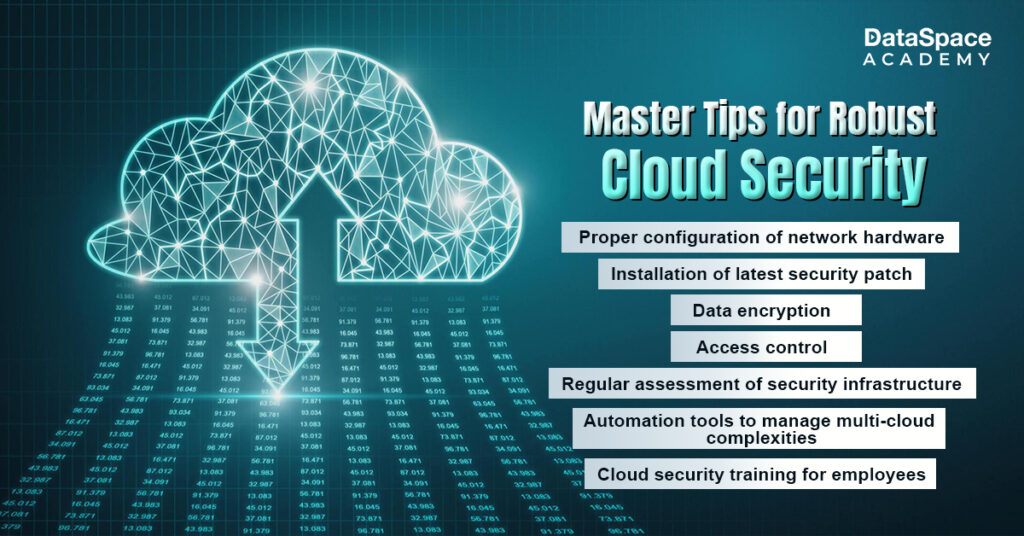
To combat the rising security risks, experts recommend the following measures:
As organisations increasingly rely on cloud services to streamline operations and data sharing, the need to protect this data from unauthorised breaches becomes paramount. Effective data security measures not only safeguard confidential information but also uphold trust and credibility with customers and stakeholders. Ultimately, prioritising data security in the cloud is essential for maintaining business continuity, compliance with regulations, and safeguarding against evolving cyber threats.

 2024 is marked by a surge in highly evolved threats that are challenging the very foundations of cloud security infrastructure. Listing below some of the following:
2024 is marked by a surge in highly evolved threats that are challenging the very foundations of cloud security infrastructure. Listing below some of the following:
 To combat the rising security risks, experts recommend the following measures:
To combat the rising security risks, experts recommend the following measures:
