API channels serve as the gateways to 83% of web traffic flows. Thus, ensuring API security is a must for organisations to facilitate seamless interaction between websites and visitors. But did you know that almost 94% of the organisations have hidden vulnerabilities in their APIs? Hackers are always sniffing out for vulnerable APIs and lack of cyber defense could lead to devastating consequences. This is where
API penetration testing comes to the rescue.
If you are new to the API pentesting world, here is your absolute guide.
API penetration testing is the process of verifying application security by emulating the attack methodology of real hackers. Pentesting helps to detect vulnerabilities, flawed configurations, and designs so that they can be addressed immediately before hackers can get to them.
In other words,
security testing for API builds the first line of defense for API channels in the battle against cyber attackers.
API pentesting within the SDLC (software development lifecycle) is the cornerstone of maintaining and updating an organisation’s overall cyber security health.
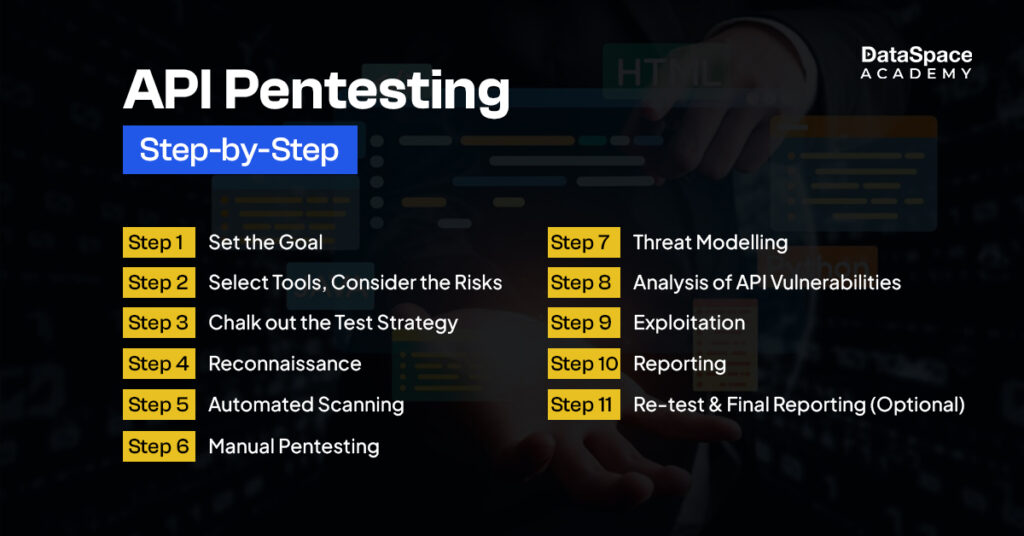
During an API security testing, a pen tester performs the following functions:
Some popular api security testing tools include Burp suite, Nmap, Akto, Postman, and ZAP.
API penetration testing is primarily conducted to secure integrated business applications for immuning the API channels from potential vulnerabilities. Regular API pen testing empowers organisations to significantly reduce the risks of potential breaches, and also comply with security standards.
API or
mobile app pentesting involves a combined strategy of automated scanning and manual testing for generating accurate and detailed security reports.

Some of the major benefits of API penetration testing include the following:
The API penetration testing is mandatory preventive approach that every online business must prioritise before it's too late. The process ensures the protection of businesses from any sort of cyber threat by utilising manual and automated API scanners. DataSpace Academy's
penetration testing certification covers various types and methods of penetration testing, offering both theoretical insights and hands-on experience to master the processes involved in effective cybersecurity assessments.


 Some of the major benefits of API penetration testing include the following:
Some of the major benefits of API penetration testing include the following:
